uno reverse card
tags: braindump
is it just me, or am i paranoid? not every day you get an attempted social engineer attack from an potential insider threat, i suppose. i am documenting my analysis of a conversation that i had with a coworker that seemed a bit out of place.
// message analysis >
so, earlier today, i received a message from a coworker. he had a question on which malware sandbox or analysis tools i use. i gave a quick reply stating that i use vt and crowdstrike’s sandbox without additional context to see where the conversation was going.
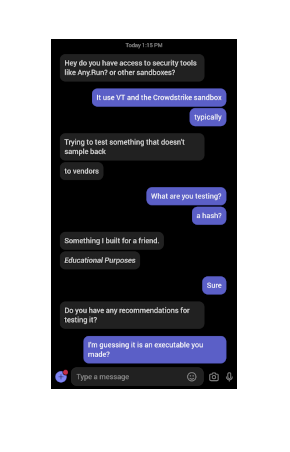
first image: shows the initial request, followed by the justification of i built this for a friend and that it is for educational purposes. then i’m asked how i would go about testing it, but i don’t provide any info and instead ask more questions.
my impression: he wrote a program and wants to run some analysis on it. ok, sounds good so far. i am interested in malware analysis, and i don’t mind sharing my perspective. however, i need more information.
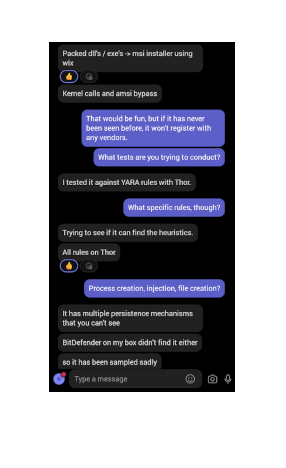
second image: he gives up more details on what he is working with; packed libraries and executables, msi package, syscalls, antimalware scanner bypass, persistence, etc., but nothing too specific. he tells me that he ran it against a bunch of yara rules and it didn’t get picked up. bitdefender didn’t pick it up either.
my impression: my spidey sense is yelling at me. is this a remcos? perhaps another payload generated by a c2 framework? why the msi package and not fileless pe hidden inside of a stager? let’s see where this takes us.
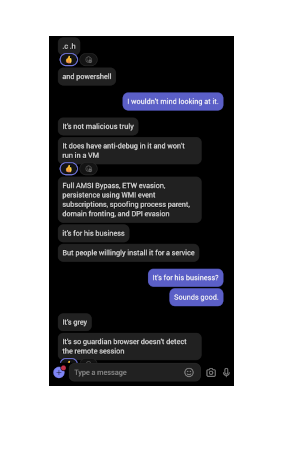
third image: he provides a little more detail. it was written in c and powershell, and has anti-debug and VM detection capabilities. he reitterates the evasion and anti-logging functionalities, but throws out some additional iocs in the mix. again, he tries to reassure me that it is truly not malicious, it was built for his friend’s business, that people willingly install this as a service, it is grey, and that its purpose is to deceive guardian browser.
my impression: bullshit. you’re telling me, after describing a fuckin’ rat and stager, that i’m supposed to believe this is greyware and that it isn’t malicious? all for what, to bypass a proctoring software? what the actual fuck?
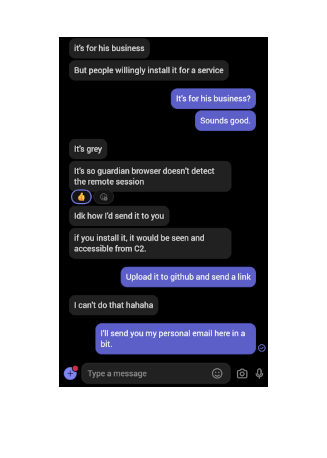
fourth image: he adds that it will be seen from a c2 if it is installed. he asks for a way to send it to me, so i picked out a gmail account that i took over a while back and dumped it in chat. obviously he can’t make this publicly available on github as that would risk it getting analyzed and detected by EDR vendors.
my impression: ah, greyware that hooks back to a c2… got it. i’ll play along with his little game–that is, if he actually decides send the files over. i’d expect him to make up a quick proton or tuta account to do so, but we’ll see if he can manage to think that far ahead.
// eof >
i’m not going to sit here and pretend i’m the best at social engineering, but holy shit was this terrible. i suppose this is what happens when an over-zealous skid gets his hands on a new toy.
part of me still thinks i should give him the benefit of the doubt and think of it as just posturing by an insecure, attention-starved douchebag.
what the fuck ever. if he decides to send over some malware, i’ll see if i can do a write-up on my analysis of it.
// alternate ending >
i didn’t want to remove anything from this post because i don’t really care about my initial thoughts on this being incorrect, but i got bored enough to actually look into the topic of vm detection bypass. it seems i jumped the gun a bit on this one, but it still has me wondering what this conversation was really about considering this is only the second conversation i’ve had with this guy.
using some dorks, i found a repo for a tool called hypervisor-phantom, but the original user is no longer on github. i found a few forks, including one that mentions bypassing proctoring software with last commits from half a year ago. one of the newer forks claims that it is for advanced malware analysis, which is a fair point since it can be used to defeat vm detection in malware, but i think that shows what the original intention behind it was.
there is another repo for a tool called vmaware that does the opposite, but is also ties back to the same user.
in the end, if you like cheating on your exams, i don’t give a shit. it’s not my place to say anything or even give a fuck about it. that aside, the process is definitely intriguing.
thanks, i guess. i learned something today.
- an0malous